I will bug bounty hunting
About the service
Initial Consultation:
Detailed discussion to understand security concerns, priorities, and objectives.
Thorough Scoping:
Define engagement scope, identifying specific areas and assets to be tested for focused efficiency.
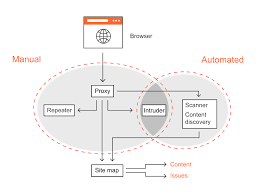
Strategic Bug Hunting:
Systematic examination of the digital ecosystem, uncovering vulnerabilities through powerful tools and personalized testing patterns.
Detailed Reporting and Collaboration:
Receive comprehensive reports on identified vulnerabilities with strategic mitigation recommendations. Collaborate seamlessly for robust solutions.
About the seller
0.0
This service
All services
Be the first to rate this service
Frequently asked questions
The Initial Consultation involves a detailed discussion to comprehend a client's security concerns, priorities, and objectives. It is a crucial step to align the security testing with the client's specific needs and goals.
Thorough Scoping is the phase where the engagement scope is defined, and specific areas and assets are identified for testing. This ensures focused efficiency in the security testing process by narrowing down to the most critical elements of the digital ecosystem that require examination.
Strategic Bug Hunting involves a systematic examination of the digital ecosystem, utilizing powerful tools and personalized testing patterns. This method aims to uncover vulnerabilities strategically, ensuring a thorough and effective identification process for potential security risks.
Clients can expect to receive comprehensive reports detailing identified vulnerabilities along with strategic mitigation recommendations. The emphasis on collaboration ensures a seamless exchange of information, enabling clients to actively participate in developing robust solutions to address the identified security issues.
Collaboration plays a vital role in the security testing process by fostering effective communication between security experts and clients. This ensures that the identified vulnerabilities are addressed collaboratively, leading to the development of robust solutions and an overall enhancement of the security posture.